|

Before starting, insure that your Systems Administrator has CONFIGURED your
privileges to allow you all of the features you will need from the LOCKSHOP
Module. Other aspects of the LOCKSHOP module are listed and linked
in the column to the left.
The LOCKSHOP is where all of your security work is accomplished for
Keys and other traceable objects. We start by associating bittings with
Blind Codes or Key IDs (they are the same). Then we associate that
information with:
 |
Issue Location
(if
Multiple Key Issue feature is used [MKI]) -
keys are normally issued from an issue point, or in the
case of MKI, multiple issue points. This issue point may, or may
not, be the lockshop; so KeyNET treats the issue point as a separate
entity even if they are combined in one location. This further
adds to the security of restricting what individuals are able to see,
create, modify, delete or otherwise control. |
 |
Hook Number - the actual residence where a KeyID
may have keys stored when not issued. Most commonly, these are
numbered hooks in a key cabinet, vault , safe, electronic key dispenser,
or other secured area where keys with the same KeyID are kept for easy
access. |
 |
Number of Keys Cut
- all of the keys ever cut in the
systems are recorded together with their histories, from creation to
destruction. |
 |
Location of Cylinder Cores
which have been pinned to that Key ID -
cylinder locations are stored in KeyNET, both current and a
history of moved cylinder locations. |
 |
Department Association
-
Keys are associated to a
department or departments. This allows for attaching Authorizations to
KeyID's and tracking keys issue to a department, as well as billing of keys
cut to a Cost Center. |
 |
Authorization assignments
for Departments & Core Locations -
Authorizations by individual can be made for an entire
department or individual rooms. An unlimited number of rooms may be
assigned to an individual even if the individual does not have authorization
privileges for an entire department. |
 |
Recall KeyID
- provides KeyNET users with the
ability to tag and track keys which have been recalled |
 |
Billing and Cost Center Use |
You will see the following items listed in the LOCKSHOP
list if you have privileges to view this area of the program. Click on an
item below to get a more detailed description of how to use them.
It is important to remember that you should have your MKI
(Multiple Key Issue) location programmed into your "My Preferences" before
attempting to issue keys, or other accountable items.
You have complete control of how you create bittings and
masterkey systems;
including
You can create
complete
masterkey systems, or simply start
by defining a key:
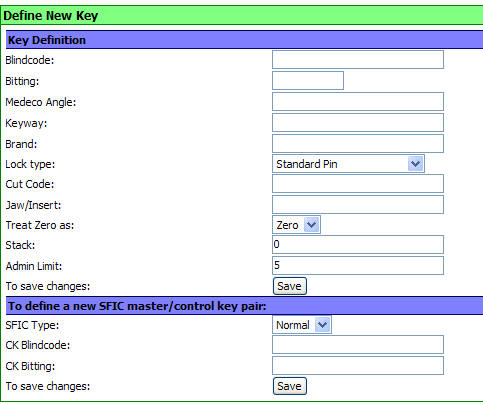
Click on the KeyNET link in the main menu bar, and then on the CREATE link to
reach this screen.
Notice that there are number of items listed that are
related to how the cylinder is pinned and the keys are cut. Additionally,
you can set Admin Limits, which will remind you when you need to obtain
permission to create more keys, or to warn administrators when they have issue
too many keys.
- KeyNET provides you with Pinning Charts to expedite your pinning of
cylinders (no more paper and pencil to figure out how to pin a cylinder).
- KeyNET takes full advantage of being able to use a Computerized Key
Machine to create keys. We have found that the time and material saved
by using this type of machine will pay for itself VERY quickly.
After you have Defined a KEY, individually or from a
masterkey system, you can SEARCH for the key. KeyNET remembers the
hierarchy of all masterkey systems it has created and provides that information
in a number of ways...you choose which works best for you.
Displaying of
"Bittings"
Bittings are a critical item in the generation of a
key. Typically, only Systems Administrators and lockshop personnel should
be able to view bittings in the KeyNET program.
Only Systems Administrators and users with Lockshop
privileges can view bittings. Additionally, in the Lockshop Privileges,
there is a BITTINGS check box. If the box is unchecked only the Systems
Administrators and Lockshop users will be able to see those bittings. If
the box IS checked for an access group, those individuals in the Access Group
can change and modify bittings in addition to being able to view them.
|